What is Phishing?
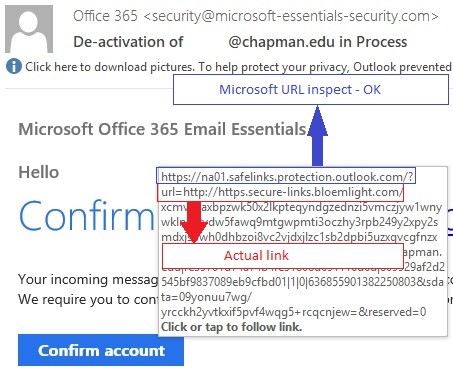
"Phishing" is a social engineering technique used to trick users into providing their personal information such as usernames, passwords, credit card details and social security numbers by pretending to be a trustworthy entity.
It often uses forged or look-alike email addresses and compromised websites that mimic the look and feel of the legitimate websites.
Phishing emails can be used to compromise an individual’s personal information or an Institution’s infrastructure and proprietary information.
The term is a homophone of “fishing” due to the similarity of using a bait in an attempt to catch a victim. A list of the recent phishing emails we received can be viewed at www.chapman.edu/security